A beginner’s guide to Zero Trust
The rise of hybrid working has completely changed the security perimeter for good. Security perimeters used to be defined by your organisation’s location, as that’s where your desktops, servers and employees were. But in the hybrid workplace, this extends beyond your offices to any access point that hosts, stores, or accesses corporate resources and services. In the new world of working, employees need secure access to their resources, regardless of where they are working.
Now’s the time to rethink your security strategy. Cyber-attacks have become increasingly sophisticated, and the old castle-and-moat approach is no longer an effective method of securing your environment.
Time to ditch the castle-and-moat approach
We all know the castle-and-moat approach – defend your perimeter while assuming everything that’s already inside doesn’t pose a threat and is already cleared for access. Well, if you’re still using that mentality, it’s time to leave the castle-and-moat approach in the past. Why? It’s been proven time and time again that it doesn’t work in the modern workplace. There’s been endless data breaches as hackers have gained access inside of the firewalls and were able to seamlessly move through internal systems with minimal resistance.
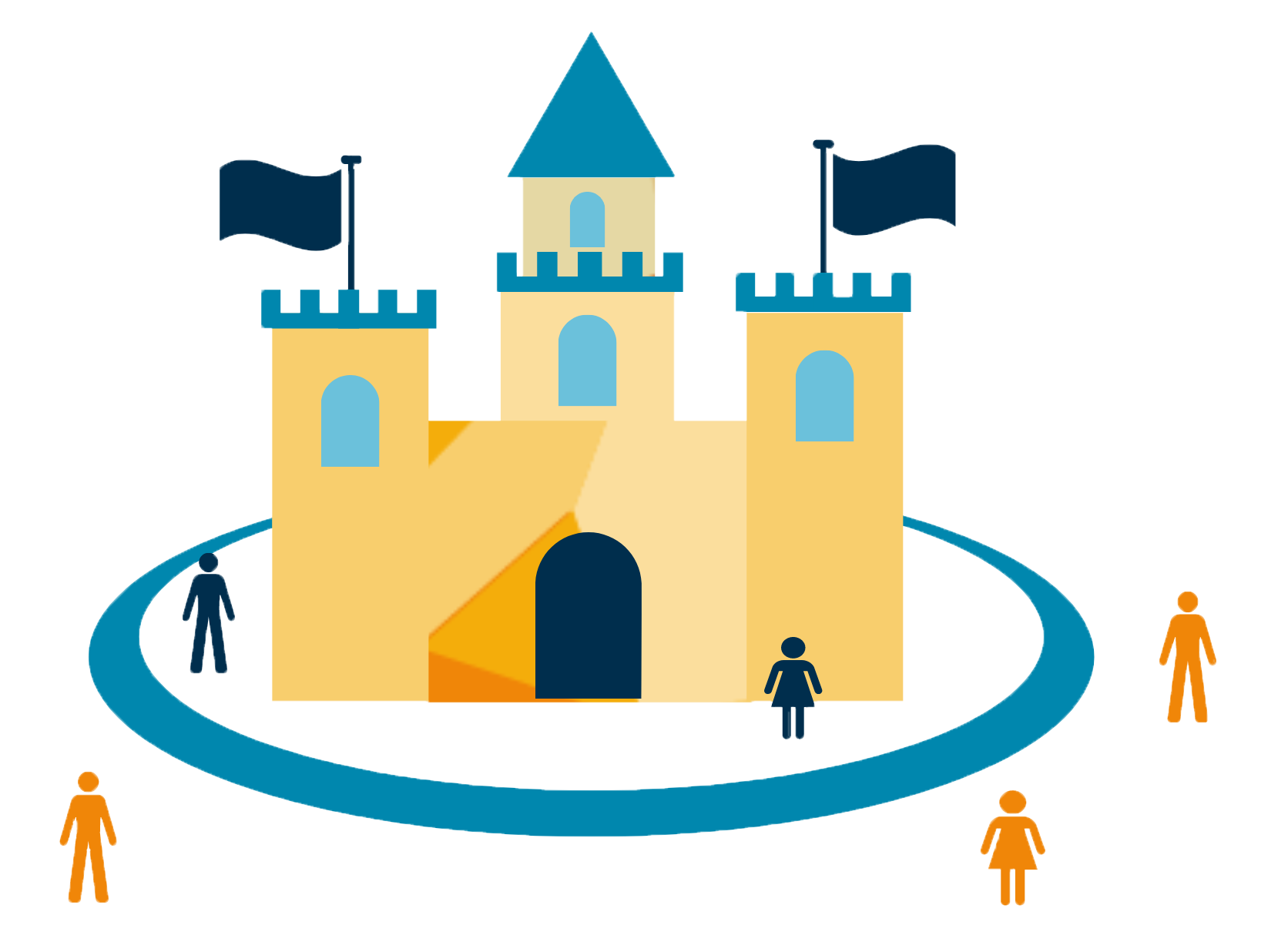
Traditional security practices, such as the castle-and-moat approach, are unable to keep up with the complexity of the ever-evolving workplace. Gone the days where the ‘castle’ works in isolation as it used to. Businesses no longer have data centres for a contained network, but instead, have applications both on-premise and in the cloud with different users accessing them from multiple devices and locations.
It’s important you have a security strategy in place that’s aligned with the modern, hybrid work environment which will look at keeping anything inside and outside your perimeter safe. This is why we want to introduce you to Zero Trust, an end-to-end security strategy that’s been adopted by millions of organisations across the world to protect their technology ecosystem.
What is Zero Trust?
Zero Trust Network is a security best practice model which was created back in 2010. Over a decade later, IT managers across the world are implementing Zero Trust as their security strategy. It’s never been easier to adopt a Zero Trust approach as more common technologies, such as Microsoft’s security solutions, are supporting it. Simply put, the Zero Trust concept is built on the belief that businesses shouldn’t trust anything inside or outside its perimeters and must verify anything and everything to connect its systems before granting access.
What does this mean for you? It would require a change in mindset – instead of assuming everything behind your firewall is safe, assume breach and the need to verify each request as it comes from an open network. Zero Trust encourages you “never trust, always verify”, meaning no cyber attack slips through the gaps. Having a Zero Trust security strategy means:
- Any access request should be authenticated and authorised before granting access.
- You should utilise analytics to detect and respond to any anomalies in real time. Mitigating any risks before they become a real threat.
- Microsegmentation and least privileged access principles are applied to minimize lateral movement
- Leverage analytics to identify what’s happened, if anything was compromised and how to stop it.
The three guiding principles of Zero Trust
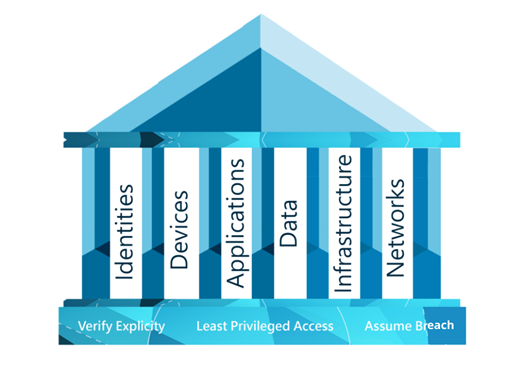
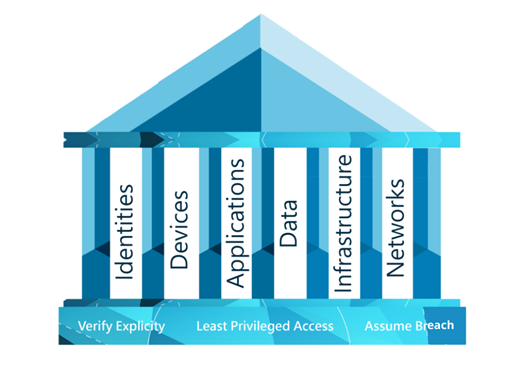
There are three principles that a Zero Trust strategy is built on; verify explicitly, use least privileged access, and assume breach. When you have a Zero Trust strategy in place, these three principles should be at the heart of your IT and at the forefront of your mind.
| Verify explicitly
Always authenticate and authorise data points. This includes identity, location, device and workload. |
Use least privileged access
Limit user access in order to protect your data. |
Assume breach
Verify that all end points are encrypted end to end. Leverage analytics to get visibility, drive threat detection and improve defences. |
These principles will help you build a solid foundation to start defending the six elements Zero Trust helps you defend.
Six elements to Zero Trust
The Zero Trust security methodology is made up of six core elements: identities, devices, apps, data, infrastructure and networks. Think of these six elements as the pillars to building a Zero Trust environment. They need to be defended in order for you to stay secure, and you can do this by assuming breach.
Why you should consider adopting Zero Trust
Adopting a Zero Trust strategy will benefit your business in other ways than just protecting your business. For starters, you’ll have a true sense of how secure you truly are and will be able to better manage your overall security posture.
You’ll also have the opportunity to scale back on any overlapping security spend. Businesses can often buy security products for tactical reasons that will often work in isolation to look after a single aspect of your security. Overtime there often becomes a pileup of products that aren’t delivering optimal coverage or value for money. Adopting a Zero Trust method will help you unify your security and ultimately help you save on costs as you streamline your technologies.
Finally, there is currently a huge skills gap when it comes to cyber security, and that gap is only going to grow. As more businesses identify they can no longer trust everything within their network, and realise they need to adopt a Zero Trust approach, this can often highlight a industry wide issue that businesses across the UK are currently facing a massive skills gap when it comes to Cyber Security. But Zero Trust can help this as the methodology will help give you a clear foundation to follow. Plus. if you don’t have the in house capabilities available, then you will have the option to draw upon the expertise from a company who specialises in security. Psst… we’re a Microsoft Gold Security Partner and have a Zero Trust Assessment available, which brings us nicely onto wrapping up this blog post.
Looking to implement Zero Trust
The truth is, building Zero Trust within an organisation doesn’t happen overnight. There’s a lot of planning that’s involved. Microsoft suggests you start by evaluating your current environment, available resources and priorities. From there you can start pulling together a plan to implement a Zero Trust strategy that meets your business needs.
Implementing Zero Trust in your organisation can often seem overwhelming. The best first step is to ensure you have the right technology in place to help you enable Zero Trust. Microsoft Technologies have the security tools and features you need to implement Zero Trust – Enabling you to gain control over your organisation’s security. Head over to Microsoft’s website to find out how Bridgewater leveraged Microsoft 365 to deploy a Zero Trust security model.
As an Azure Expert MSP and Microsoft Security Gold Partner, we’re in a unique position to help you adopt Zero Trust within your organisation. Not only could we help you deploy Microsoft technologies, but we’ll also help you implement the Zero Trust best practices and framework. Simply get in touch to find out more.
Claim your complimentary Zero Trust Health Check
- Walk through your Zero Trust readiness in an exploratory 1:1 workshop
- An initial view of your security estate
- Identify cost optimisation opportunities